✖Traditional Challenges
Centralized systems are vulnerable to single points of failure, data breaches, and state-sponsored attacks.

© Copyright 2025 – Tokenize The Border, Inc. All Rights Reserved.

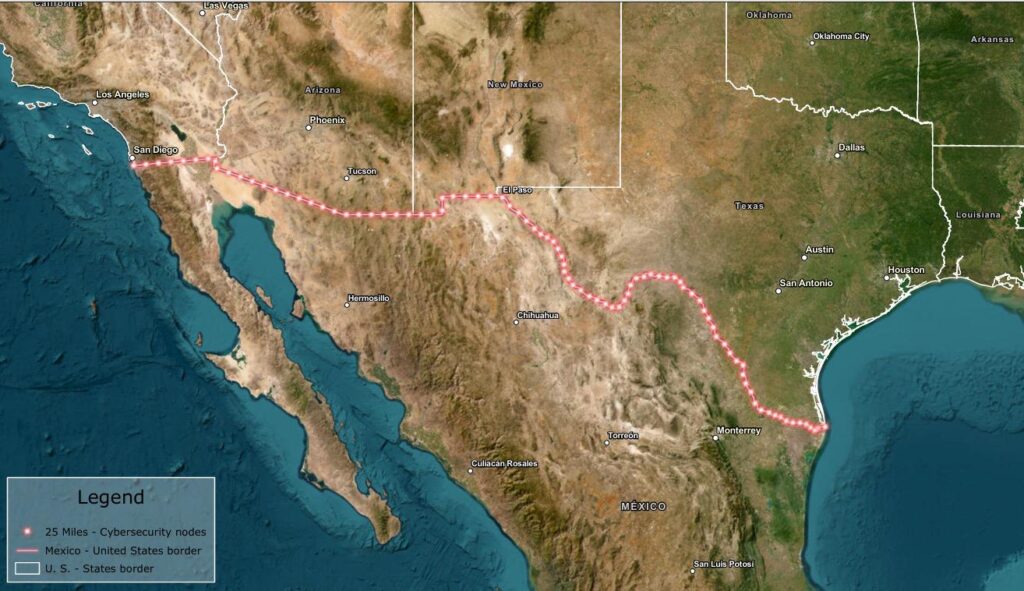
Build a decentralized network of 80 cybersecurity nodes positioned at exact strategic coordinates along the border.

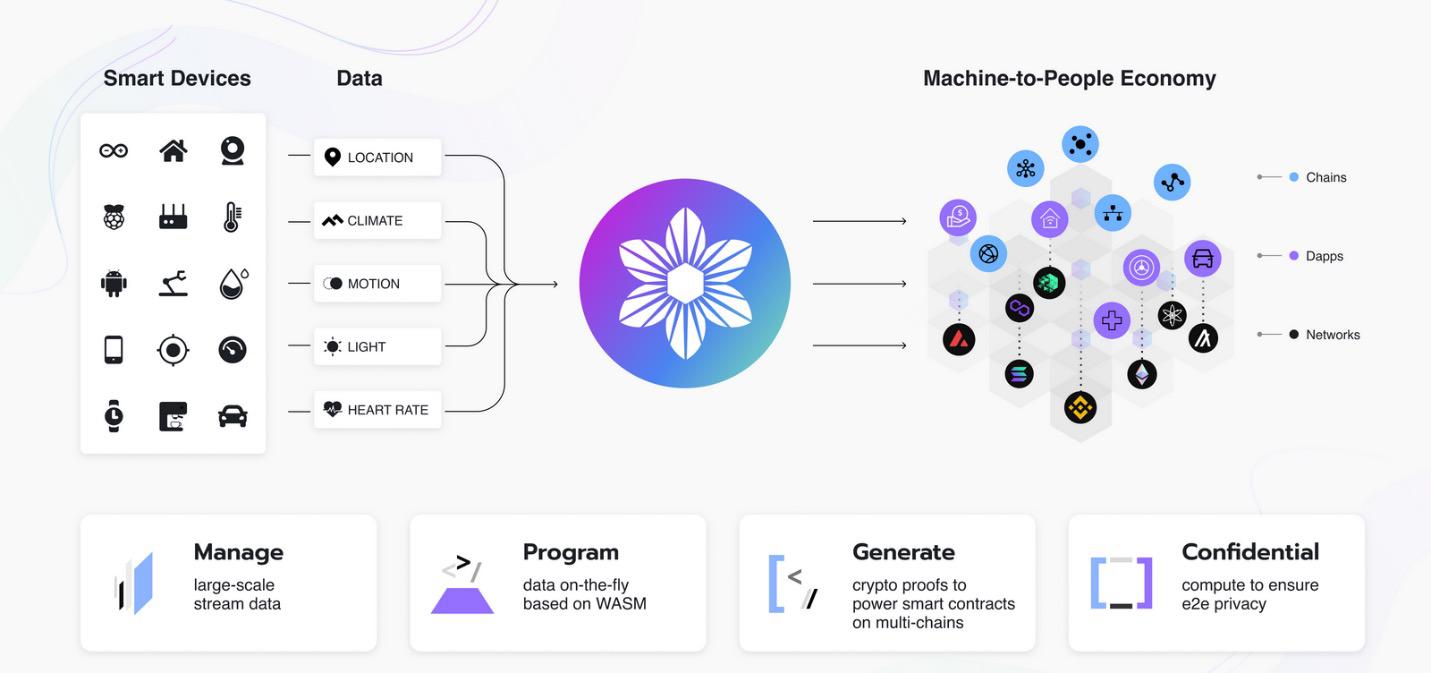
Centralized systems are vulnerable to single points of failure, data breaches, and state-sponsored attacks.
Increased redundancy, real-time threat sharing, and robust fault tolerance.